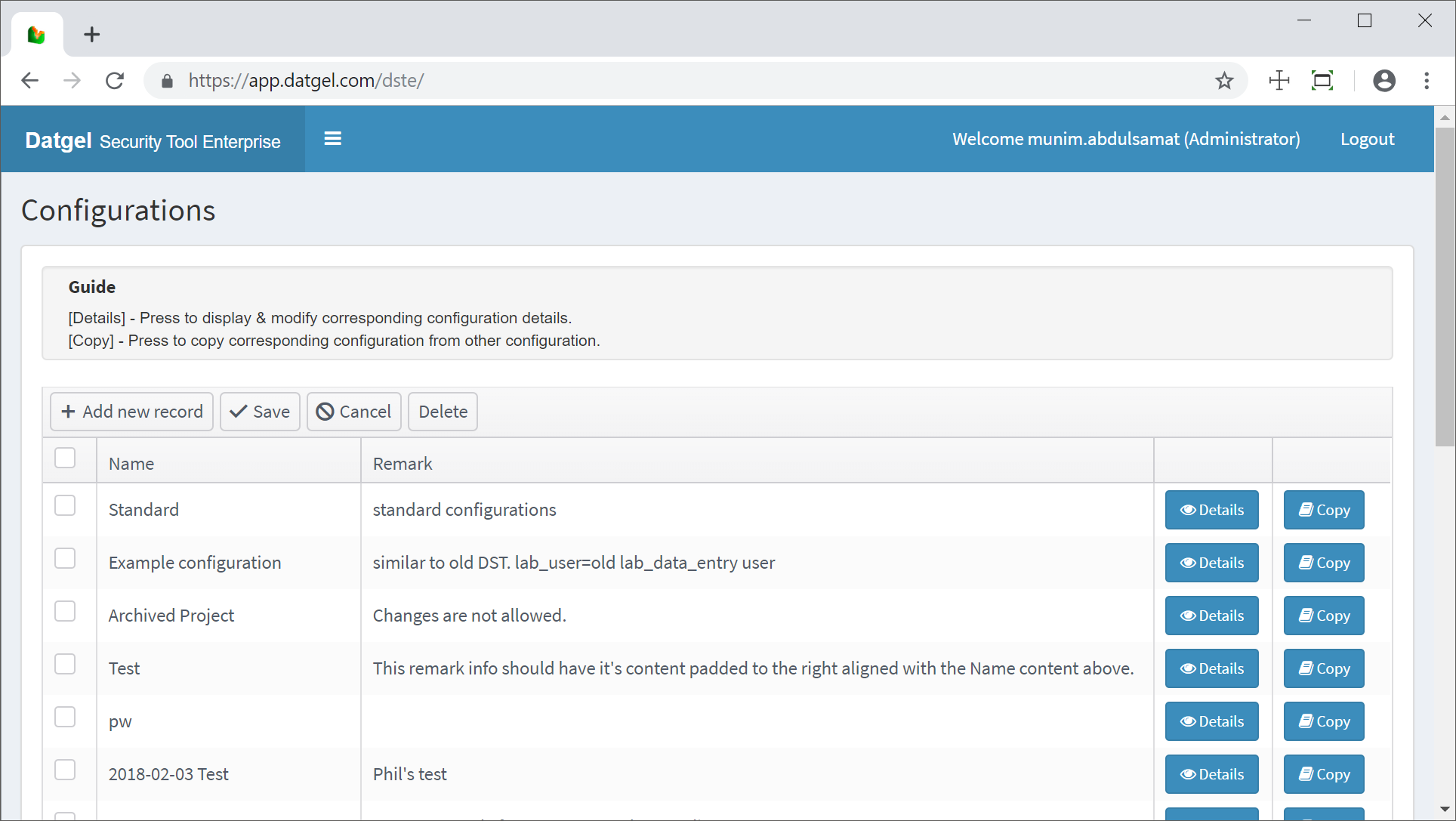
Configuration menu
This is the main configuration screen where Security Configurations are defined and managed. This screen lists all the available Security Configurations created represented by the configuration's name and remarks added to it. A Security Configuration may either be defined from scratch or copied from an existing Security Configuration. Only administrators has the privilege to create or make any amendments.
A Security Configuration is a customized group of rules/commands applicable to a specific user/group of users. For each Security Configuration, the following rules/commands can be controlled to be applied to different users or user groups according to their security status.
- Editable/uneditable and show/hide tables
- Editable/uneditable and show/hide fields
- Right to use a gINT commands
- Right to use an add-in commands
- Show/hide gINT applications or its groups
- Approve Tool related fields and tables
A configuration is independent of a database or project, and can be applied to multiple individual projects, databases or at instance level.
Example 1: A Security Configuration may be defined to apply on projects meant for archive which would not allow users to edit but only view data.
Example 2: A Security Configuration may be created and applied to current production projects where some users has limited rights to enter data, view tables related only to their area of work, limited rights to check, review or delete data, limited rights to modify report templates or full control of the entire database.
Configuration screen
| Caption | Type | Description |
|---|---|---|
| Name | Column | Security Configuration name. Mandatory. |
| Remark | Column | Additional related information. |
| Add new record | Action | Adds a new empty row for new configuration input. |
| Save | Action | Updates any changes made. |
| Cancel | Action | Undo any changes made. |
| Delete | Action | Removes selected configuration. |
| Details | Action | Step into details of corresponding configuration. |
| Copy | Action | Launch window to select existing Security Configuration to copy from. |
A complete explanation about how to manage a configuration is detailed in Setting up a Security Configuration.