Azure AD federation setup
Background
For lager organizations especially, it may be inefficient to create and manage users though id.datgel.com, particularly to remove uses when they leave the organization. It can be more efficient to use your Azure AD identity provider to authenticate users.
After the setup is complete the work flow for a user is they type their organization email into the id.datgel.com login page, and they will be redirected the Microsoft Azure AD login page, and they login using their Azure AD/Office365 credentials. Hence no need to remember yet another username and password. Users would be automatically added to the Organization Employee group in id.datgel.com upon initial login.
Overview
This document describes how to configure your Microsoft Azure AD (AAD) as an identity provider that is used by id.datgel.com for authenticating users. The process where your organization identity provider is used as a central source of identity for connected applications is called federation.
This document gives step-by-step instructions for AAD federation configuration. You will need to inform Datgel Support of some parameters to allow Datgel to configure id.datgel.com to work with your AAD.
Please note that it is required that users in Azure AD have first name, last name and email address (in contact info) specified.
Setup in Azure management portal (portal.azure.com)
From the Azure AD perspective, id.datgel.com will work as a client application. Setup in Azure management portal must be done first, and the following pieces of information need to be carried over to id.datgel.com in order to configure the id.datgel.com side of the AAD connection:
- Application (client) ID: This will be used as “Client key” value in id.datgel.com Sysadmin
- Client secret value: “Client secret” in id.datgel.com Sysadmin
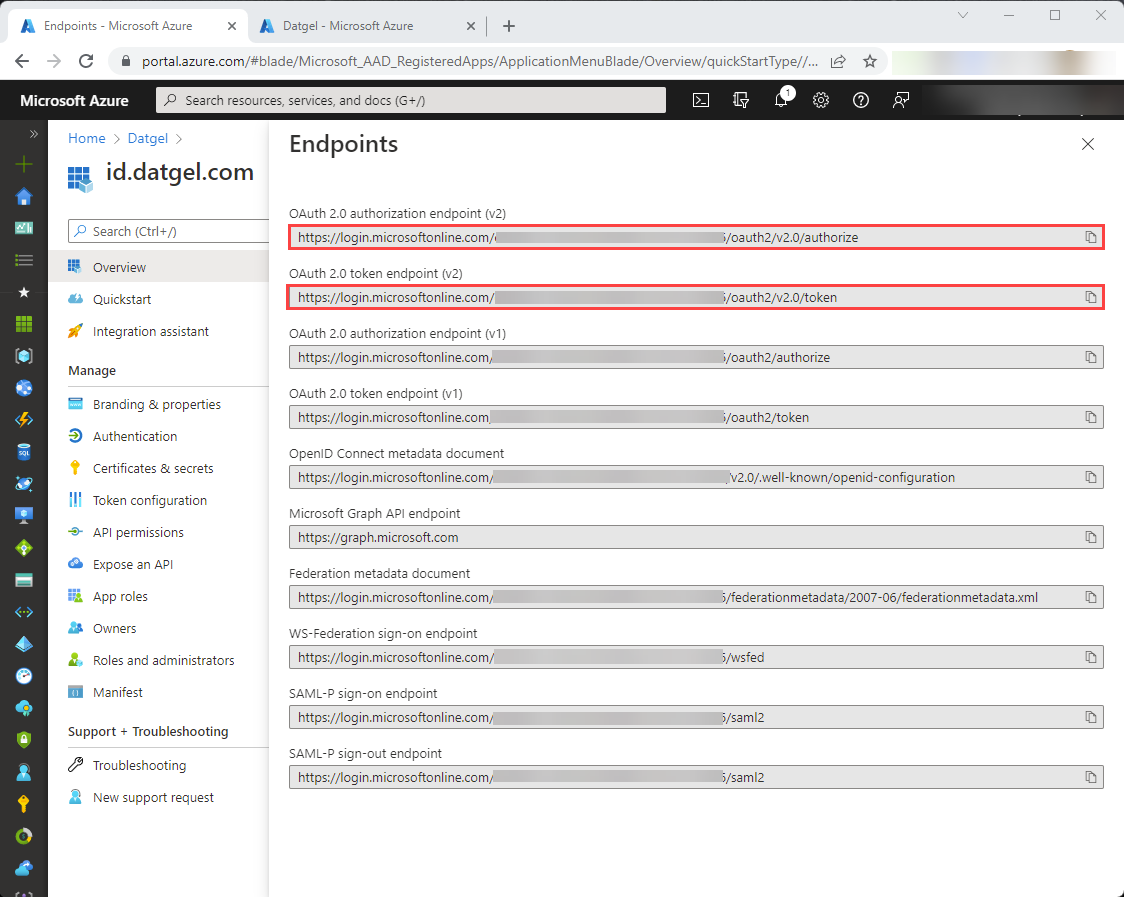
- OAuth 2.0 authorization endpoint (v2): “Authorization token URL” in id.datgel.com Sysadmin
- OAuth 2.0 token endpoint (v2): “Access token URL” in id.datgel.com Sysadmin
In this chapter, the values that are needed on the id.datgel.com side are bolded.
First step is to register the id.datgel.com application in Azure. Open AAD management portal and select “App registrations”, and select New registration.
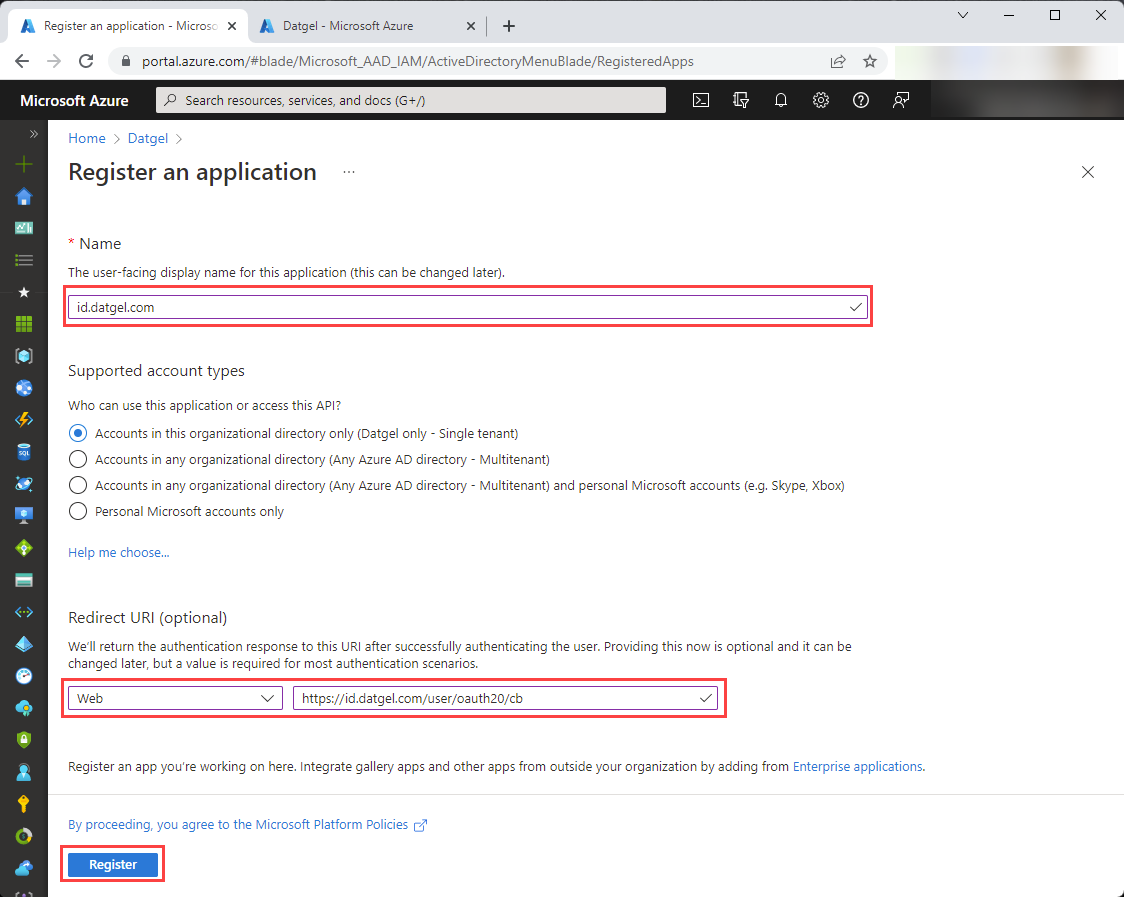
Set the Name: id.datgel.com
Under Redirect URI, select Web and set the text box to: https://id.datgel.com/user/oauth20/cb . Then click “Register".
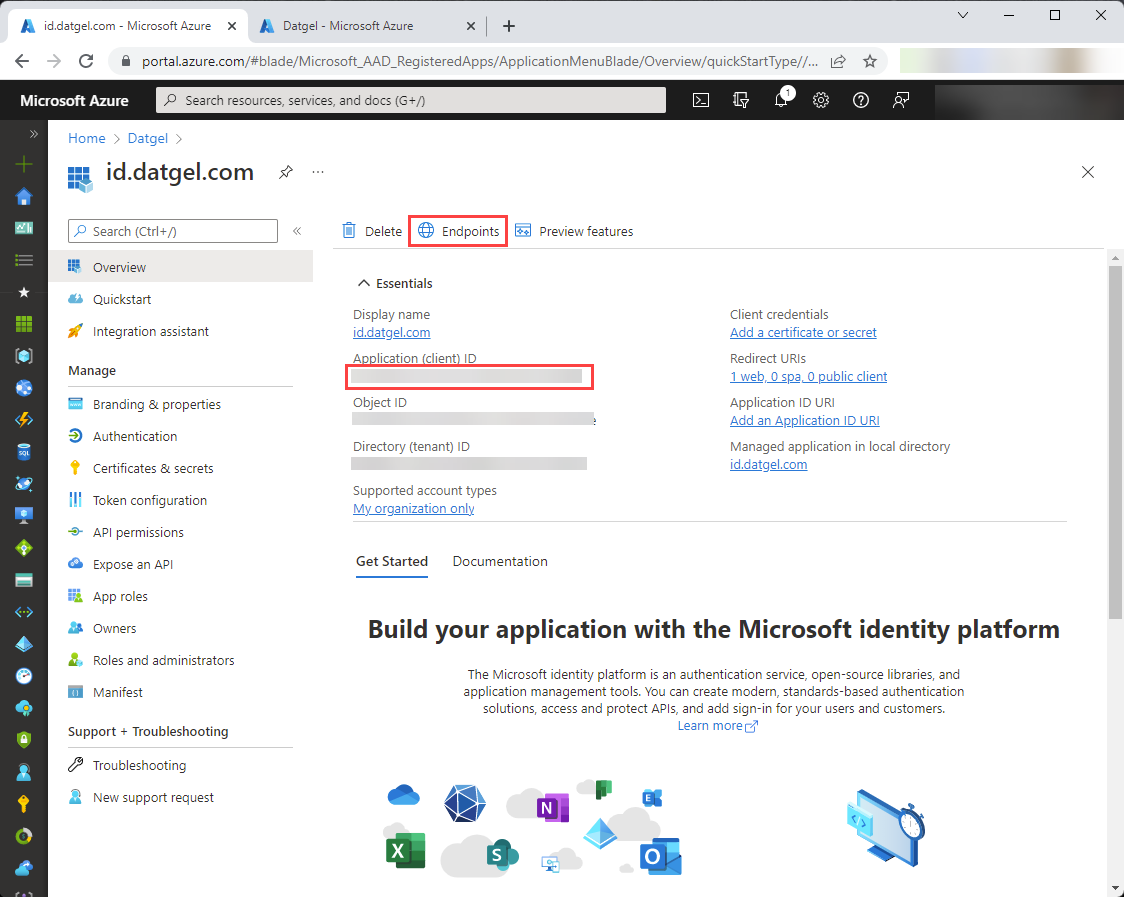
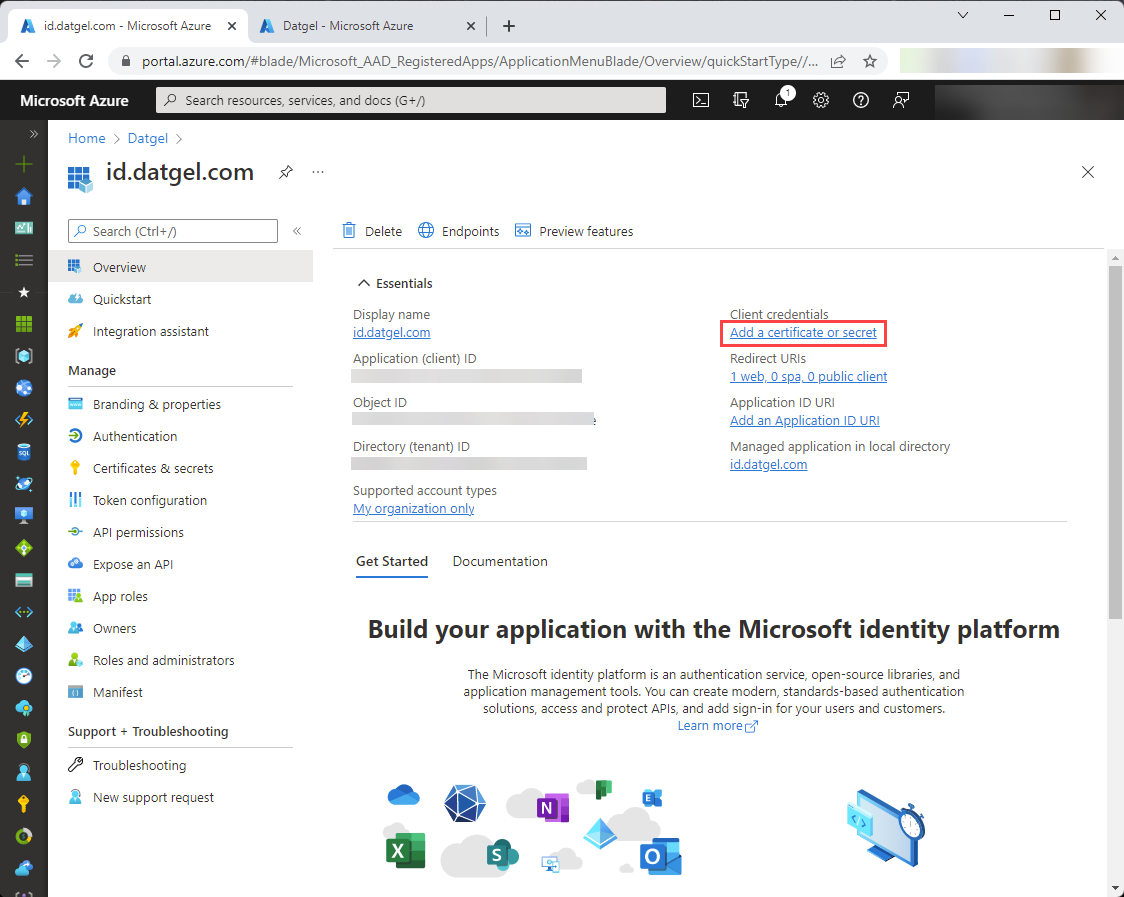
On the screen that follows you’ll see basic details of the created application registration. The “Application (client) ID” will be needed later when configuring connection to AAD in id.datgel.com.
Select Endpoints.
The first two values, “OAuth 2.0 authorization endpoint (v2)” and “OAuth 2.0 token endpoint (v2)” will be needed later when configuring the id.datgel.com service.
Now click on the X to return to the previous screen.
Select “Add a certificate or secret”.
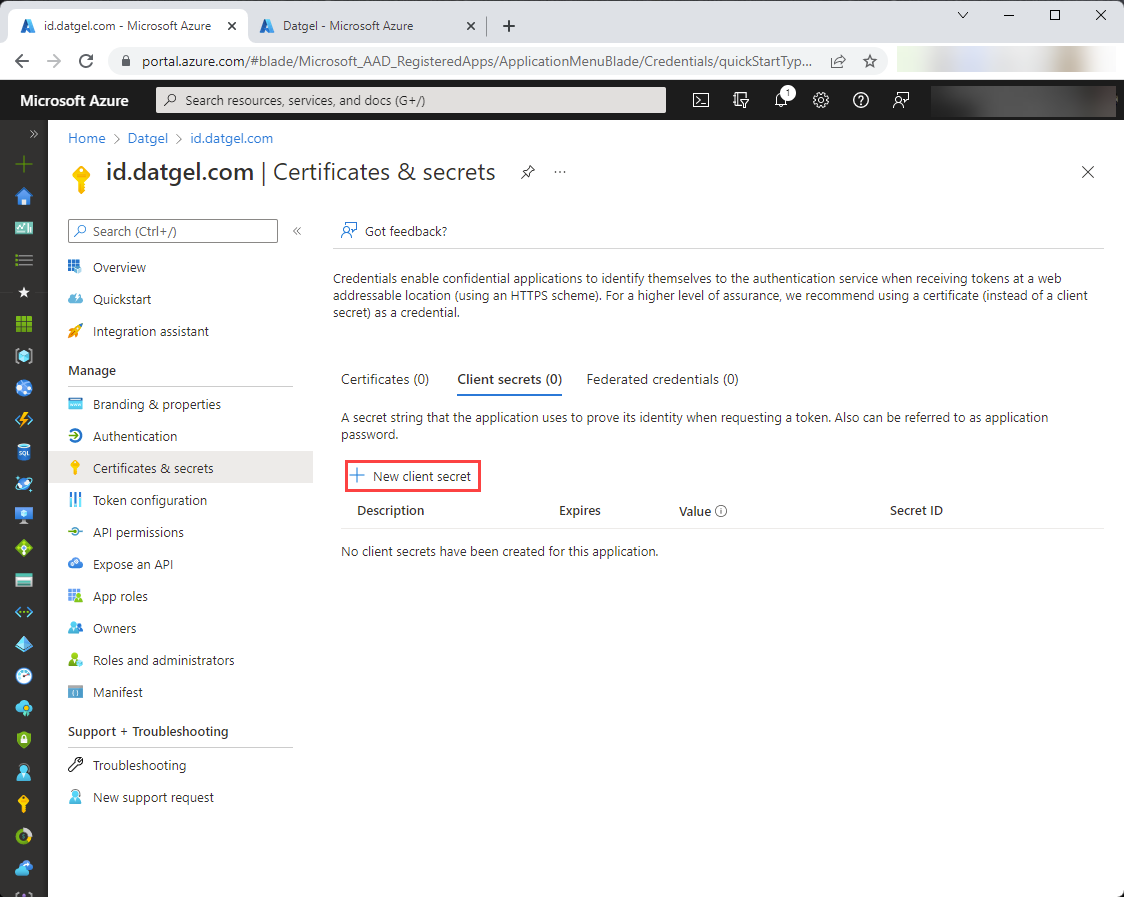
On the next screen, click “New client secret”:
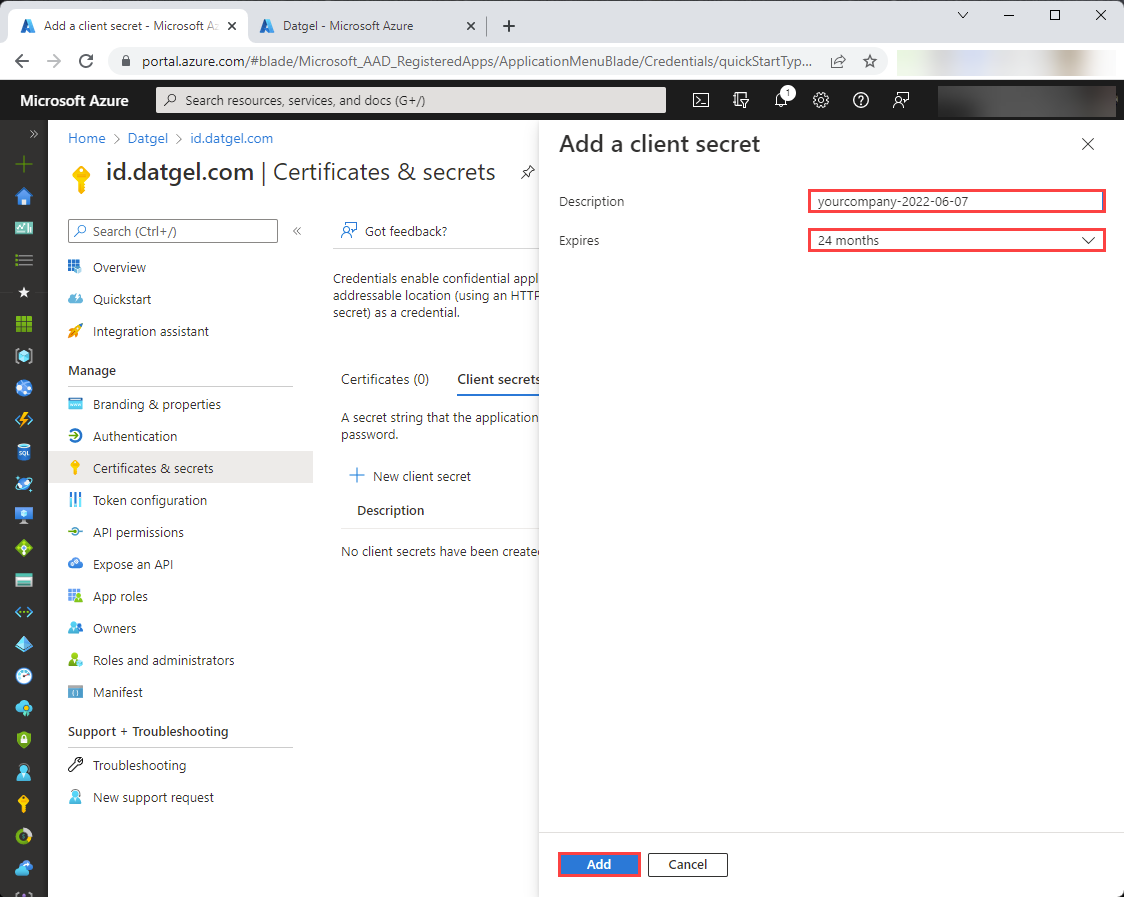
Next, give a description for the client secret to create, select your preferred expiration for the client secret, and click “Add”:
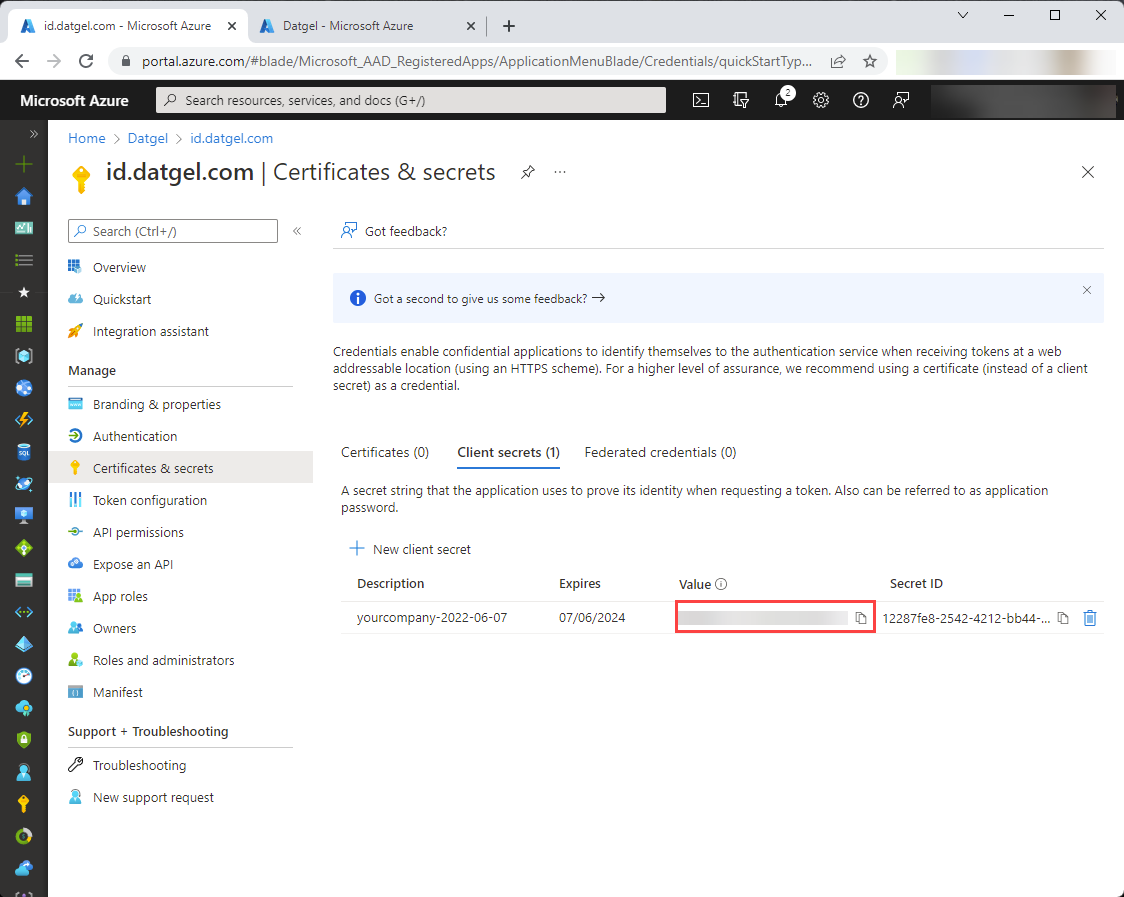
You’ll see the created client secret. “Value” and “Secret ID” are available here for copying. “Value” will be needed later when configuring the id.datgel.com service, copy it now because later it will not be visible.
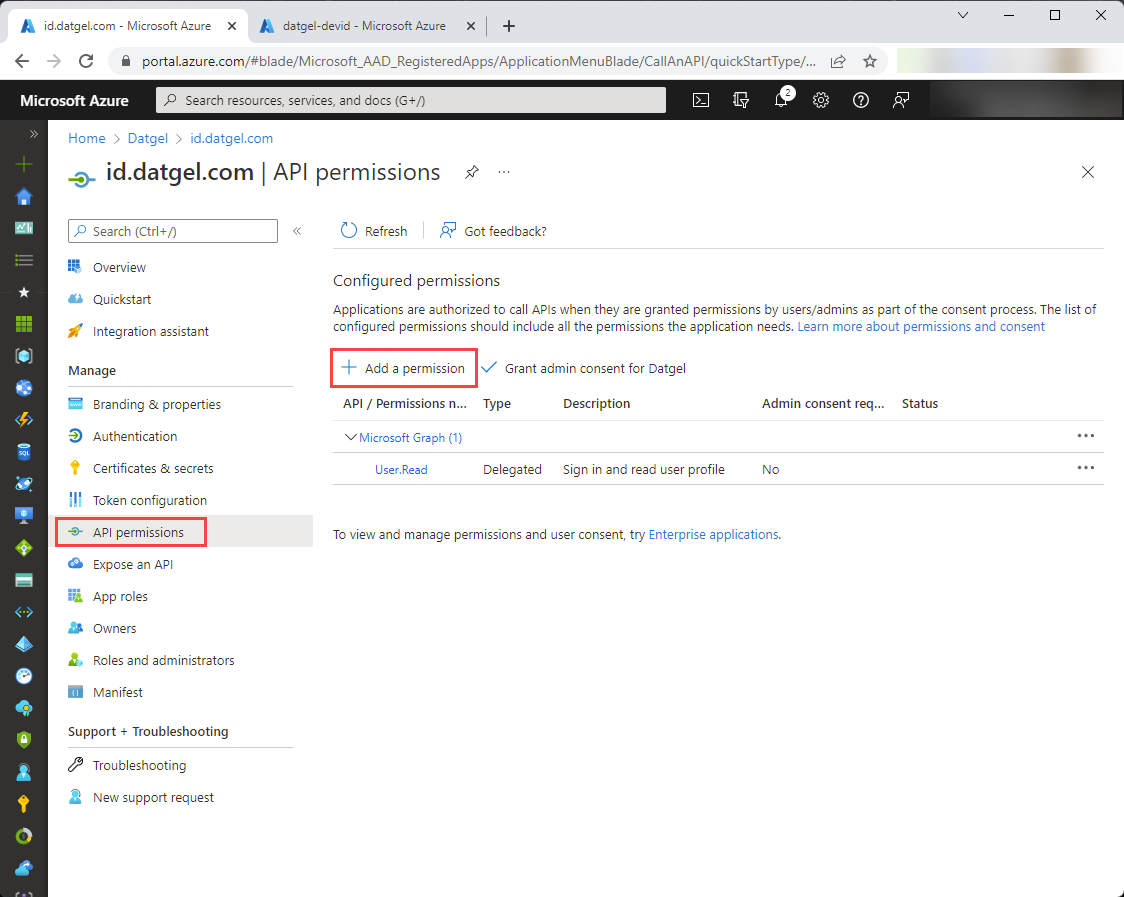
Next, Select “API permissions” in the menu ion the left
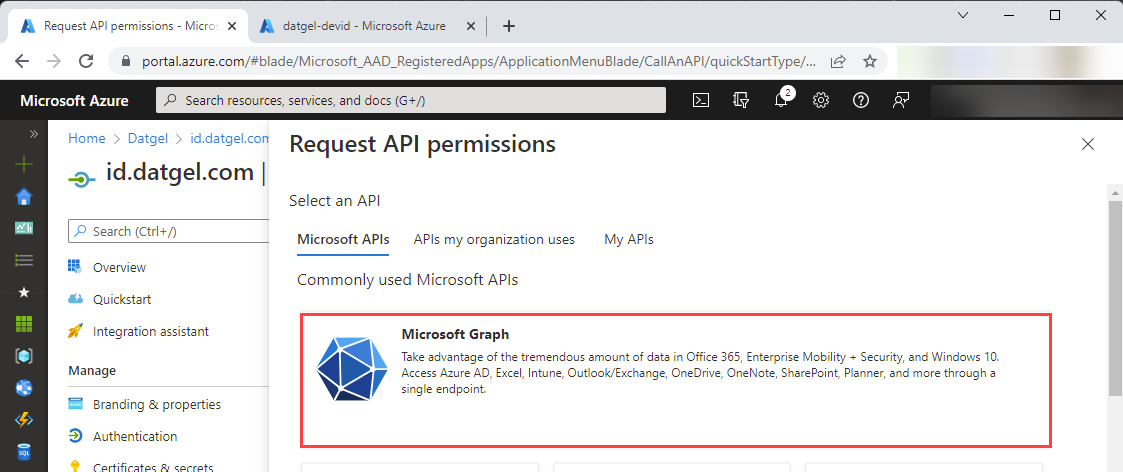
Initially created API permissions are displayed, click “Add a permission”:
Then select “Microsoft Graph”:
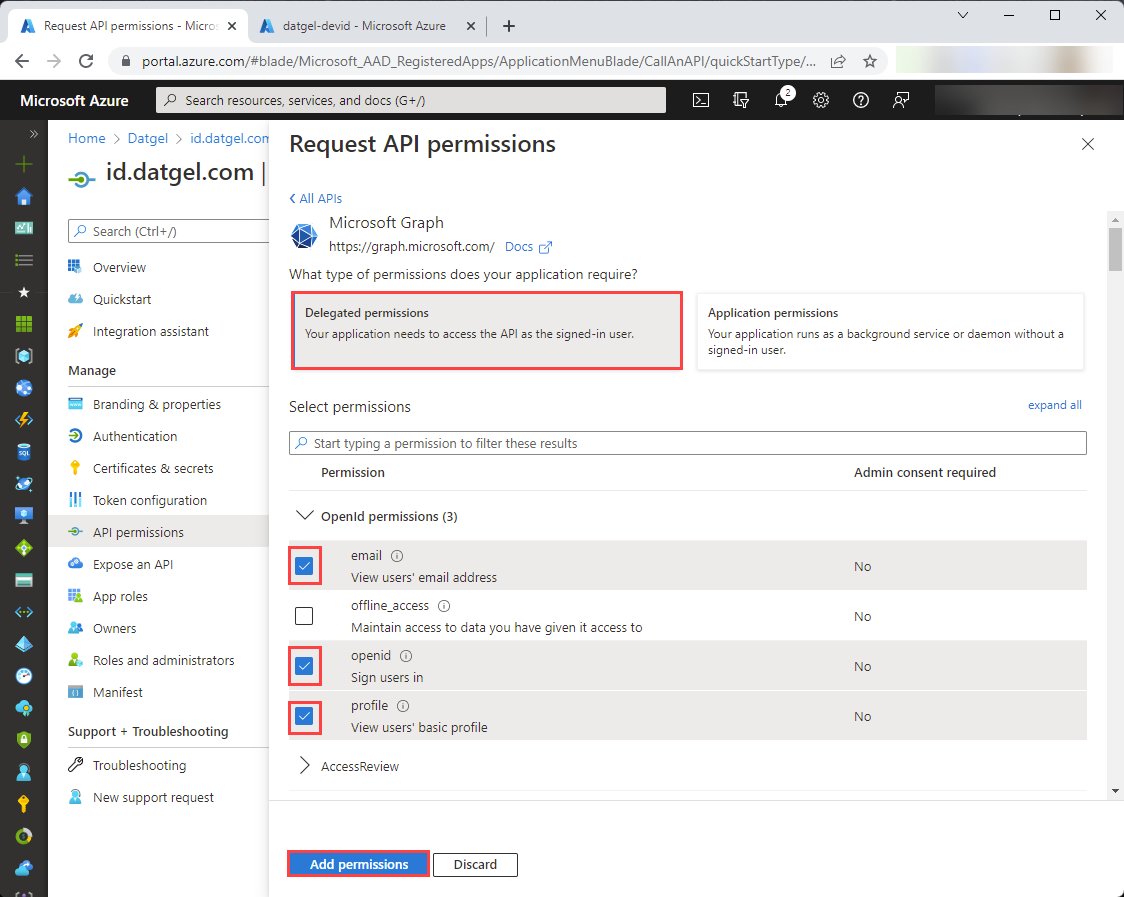
Select “Delegated permissions”.
You will see “OpenId permissions” listed on the screen. Select “email”, “openid” and “profile”, and click “Add permissions”:
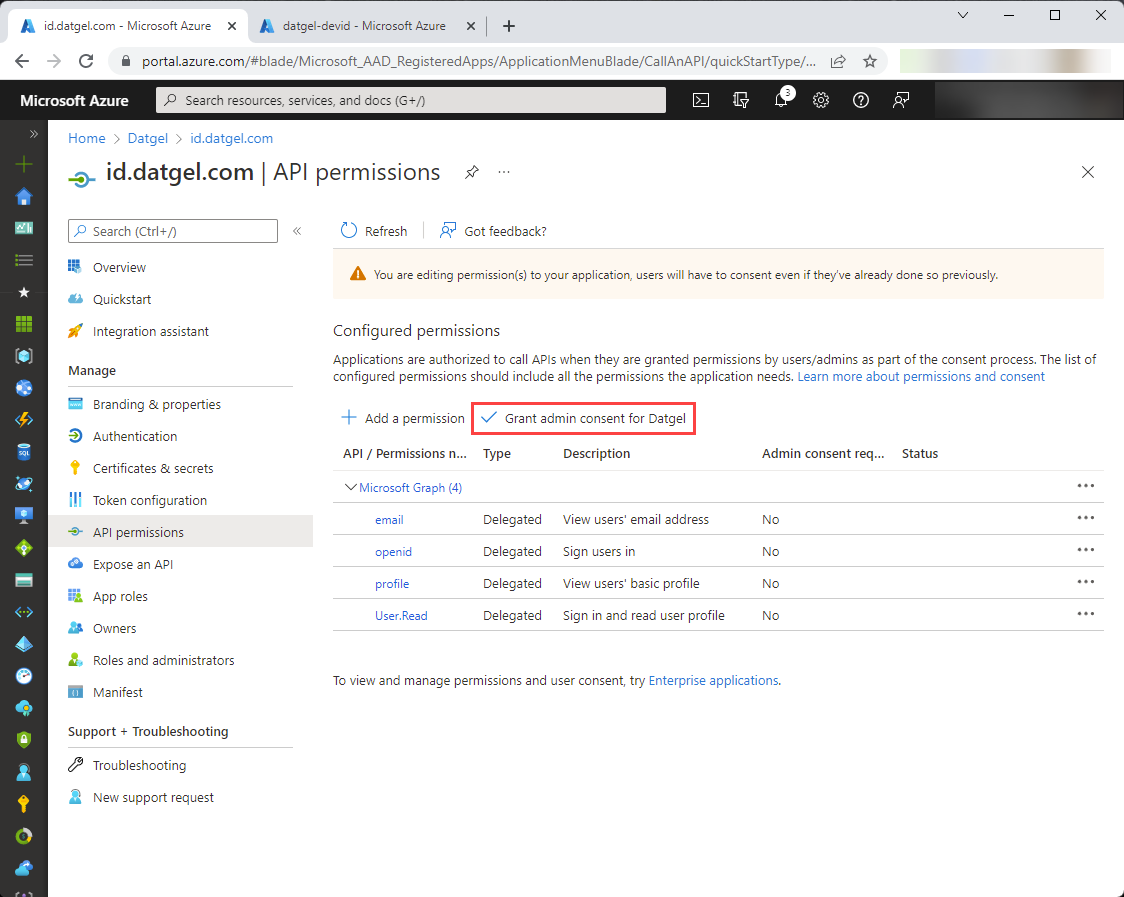
These permissions allow id.datgel.com to get basic user information (email address, user id and name) from Azure AD. Next, let’s tell Azure AD that when an end user authenticates, a separate consent will not be required from each user. Click “Grant admin consent for YourOrganisationName”, and on next screen press Yes.
Now everything is ready in AAD.
Please email the following information to support@datgel.com and request Datgel support configure AAD federation for your organization in id.datgel.com.
- Application (client) ID
- Client secret value
- OAuth 2.0 authorization endpoint (v2)
- OAuth 2.0 token endpoint (v2)
- The name of the id.datgel.com organization to federate with, which is visible in https://id.datgel.com/orgadmin
Limitation
Note at this time users can be added to one organization automatically. However, some Datgel clients have two or more organizations in id.datgel.com, one for international licenses and one for each country that has licenses. The work around is Datgel can programmatically add users in one id.datgel.com organization to another, one off/periodically upon request. We should automatically add users to country based organizations and copy them to the international organization.
Related articles
There is no content with the specified labels